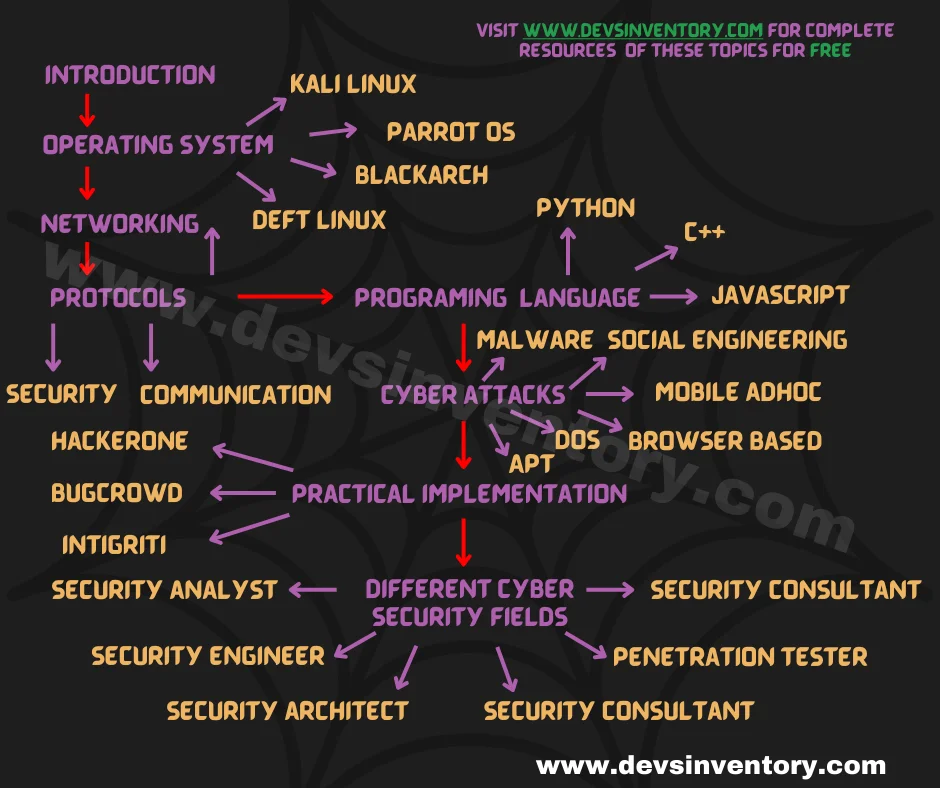
Cyber security roadmap and topics are listed in order of their level from top to bottom below
All the resources listed below are available for free on internet. the given cyber security roadmap is curated from different resources available across the internet and are selected on the basis of their approval rating*.
Click on any link to go to the source these are the best resource present currently on the internet.
Reading resource
- Introduction to cyber security – Codecademy
- Cyber security :- a step by step guide- Simplilearn
- Introduction to cyber security – HKR training
Video resource
- Cyber security full course – Edureka
- Introduction to cyber security – Simplilearn
- cyber security for beginnners – Simplilearn
Interactive playground
Online Communities
Kali linux resource
- Kali linux for beginner’s – Guru99
- Kali tools documentation – Kali org
- Kali linux tutorial – Simplilearn (youtube) 2023
- Linux for hackers – David bombal (youtube)
Parrot OS resource
- Parrot OS documentations – Parrotsec.org
- Parrot sec OS guide – Github
- Ethical hacking using parrot os – Hackerz.exposed (youtube)
Blackarch resources
- Blackarch guide
- Getting started with blackarch – Systran box
- Exploring hacker OS: blackarch – SecurityFWD (youtube)
DEFT linux resources
Essential for Cyber security
Networking for cybersecurity | what you need to know- Ryan john (youtube)
- OSI model explained – Imperva
- OSI security architecture – Interviewbit
- Network topology – Intellipaat
- 8 steps to understand subnetting – Technopedia
- Cyber security In-depth network layer – W3 school
- Default gateway – ITpro
- Subnet mastery – Practical networking
- Network troubleshooting tools – Zenarmor
- Basic of network terminology – Geeksforgeeks
- A-to-Z cybersecurity terminology – MetaCompliance
Network communication protocol
Network security protocol
Javascript resource
Python resource
C++ resources
Scripting resources
Social engineering resource
Phishing, Bating, Eavesdropping, Spoofing, Direct-access, Identity-theft, Repudiation
DOS resource
DDOS, Botnet, Tearsdrop, Smurf, Buffer overflow, Physical, Exploits, Previlage escalation attack
Malware resources
Virus, Spyware, Worms, Adware, Trojan horses, Rootkits, Keylogger, Backdoors, Ransomware
Password attack resources
Database/ Software based/ Browser based resources
SQL injection, Logic bomb, Cross site scripting, Man in the middle, Tampering
APT resources
Hactivism, Commodity threat, Cyber espionage, Indirect attack
Mobile Adhoc network resources
Byzantine, The blackhole, Flood rushing, Byzantine wormhole, Bluesnarfing, Bluejacking, Byzantine overflow network wormhole
Cyber physical resources
Basic Project resource
- code keylogger using python – Shaun Halverson
- SQL injection for beginner’s – Loi liang yang
- Caesar cipher in python – Fabio musanni
- Packet sniffer – Github
- Credit card encryption decryption – Github
Bug bounties platforms
Information security analyst
Security engineer
Security architect
Complete roadmap, essential certificates, and resources for security architect – Simplilearn
Ethical hacker
Complete roadmap, essential certificates, and resources for ethical hacker – Medium
Security consultant
Complete roadmap, essential certificates, and resources for security consultant – Simplilearn
Penetration tester
Complete roadmap, essential certificates, and skills for penetration tester – Its security guru
